Bring Your Own Key(BYOK)
Overview
Bring Your Own Key (BYOK) is a security model that empowers enterprises to retain full control over the encryption keys used to secure their data. Rather than relying on service providers to generate and manage encryption keys, BYOK allows customers to create and import their own keys into the cloud environment.
In the Netcore platform, BYOK is implemented using AWS Key Management Service (KMS), allowing customers to manage encryption for services at the database level. The encryption is applied at rest, and the customer-supplied key is never exposed to Netcore systems in plaintext, ensuring maximum security and compliance.
This is a paid feature. Contact your Netcore Support team to enable this for your account.
Why BYOK Matter(Business & Security Context)
- You control access to your data
- Your data is encrypted with a key of your own.
- If you revoke the key, your vendor will be unable to access or decrypt your data.
- Enables zero-trust architecture, full control, and lockout capabilities.
- Stronger security & compliance
- Critical for regulated industries: Fintech, Banking, E-commerce, Healthcare, Insurance
- Helps fulfill data residency and key management obligations.
- You manage the key lifecycle
You control:- Where the key is stored
- When it's rotated or destroyed
- How incident response or audit processes are handled
- Prevents insider threats at the vendor
- Even if internal teams (support, engineering) are compromised, they cannot decrypt your data.
- Your encryption key is never shared with or stored by the vendor.
- Better protection against government access
- The vendor cannot decrypt your data.
- Enables data sovereignty and key sovereignty.
- Why is this critical for marketing automation platforms?
- Personally Identifiable Information (PII)
- Purchase and behavioral data
- Segmentation logic
- Financial or transactional records
- In regulated industries, BYOK is increasingly mandatory to:
- Protect sensitive customer data
- Comply with internal policies and external regulations
Benefits of BYOK
- Full Control: Customers manage the lifecycle of their encryption keys.
- Compliance: Supports regulations
- Visibility: AWS CloudTrail enables tracking of key usage.
- Security: AES-256 symmetric encryption; key material never leaves AWS in plaintext.
- Separation of Duties: Service provider manages data; customer manages keys.
How It Works
Components Involved:
- Customer Managed Key (CMK) in AWS KMS
- Customer Encryption Key (created and wrapped by the customer)
- Data Base Stores Data (encrypted using CMK)
Process Overview
- Key Generation: Netcore generates a placeholder CMK in AWS KMS.
- Key Wrapping: Customer encrypts their secret key using the AWS-provided wrapping key.
- Key Import: Netcore imports the wrapped key into the CMK.
- Data Encryption: CMK is used to encrypt data at rest.
- Key Rotation: Performed annually or biennially as required.
Implementation
Once the KMS key is created, we can download the Import Key material, which will include three
files:
1. ImportToken.bin
2. WrappingPublicKey.bin
3. Readme.md
1. Netcore Creates KMS CMK
- Navigate to AWS Console > KMS > Customer Managed Keys > Create Key
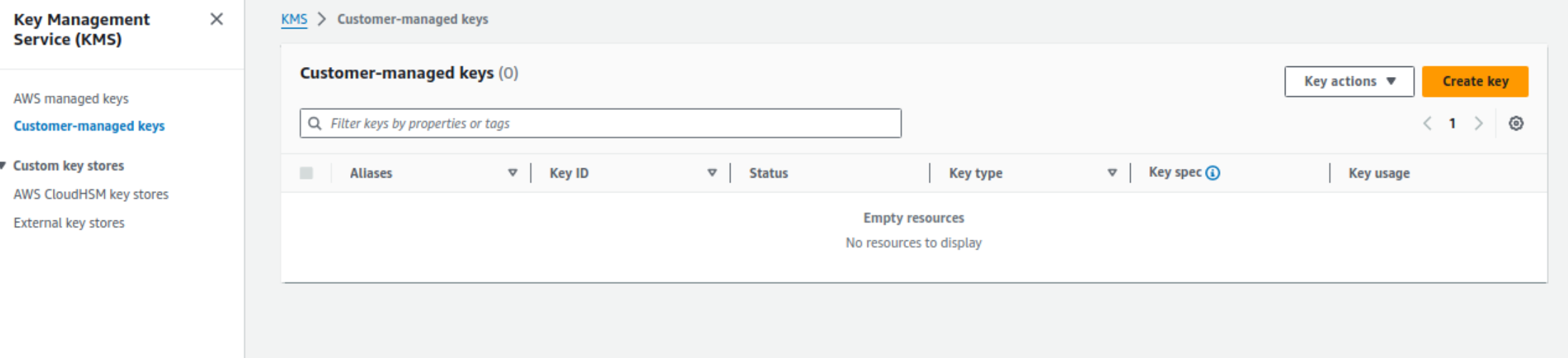
Navigate to AWS Console
- Configuration:
- Key Type: Symmetric
- Key Usage: Encrypt and Decrypt
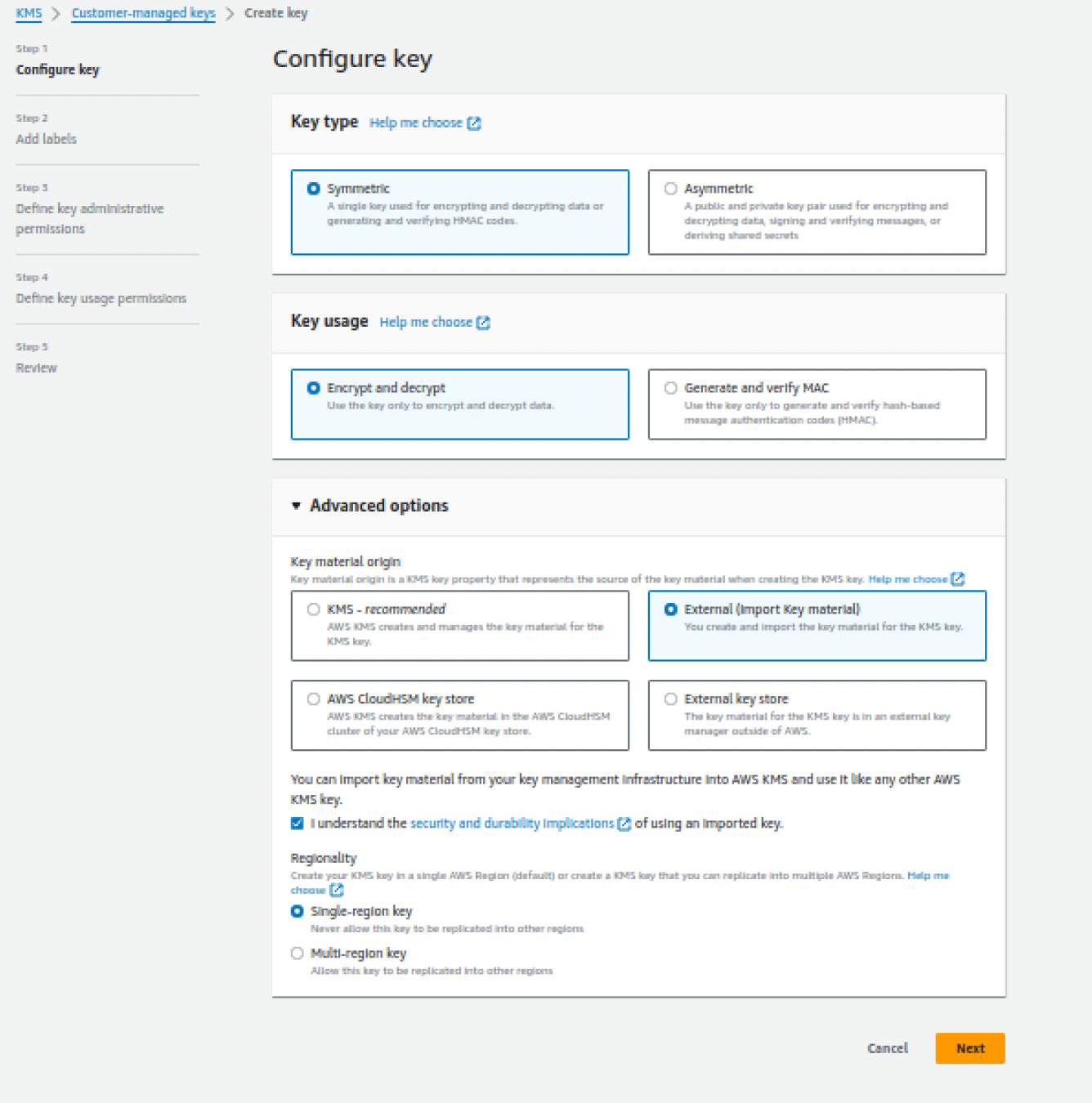
Configure Your Key
- Advanced Options:
- Key Material Origin: External (Import Key Material)
- Regionality: Single-region key
- Other Settings:
- Alias: Set as key name
- Description: Provide context
- Tags: Optional metadata
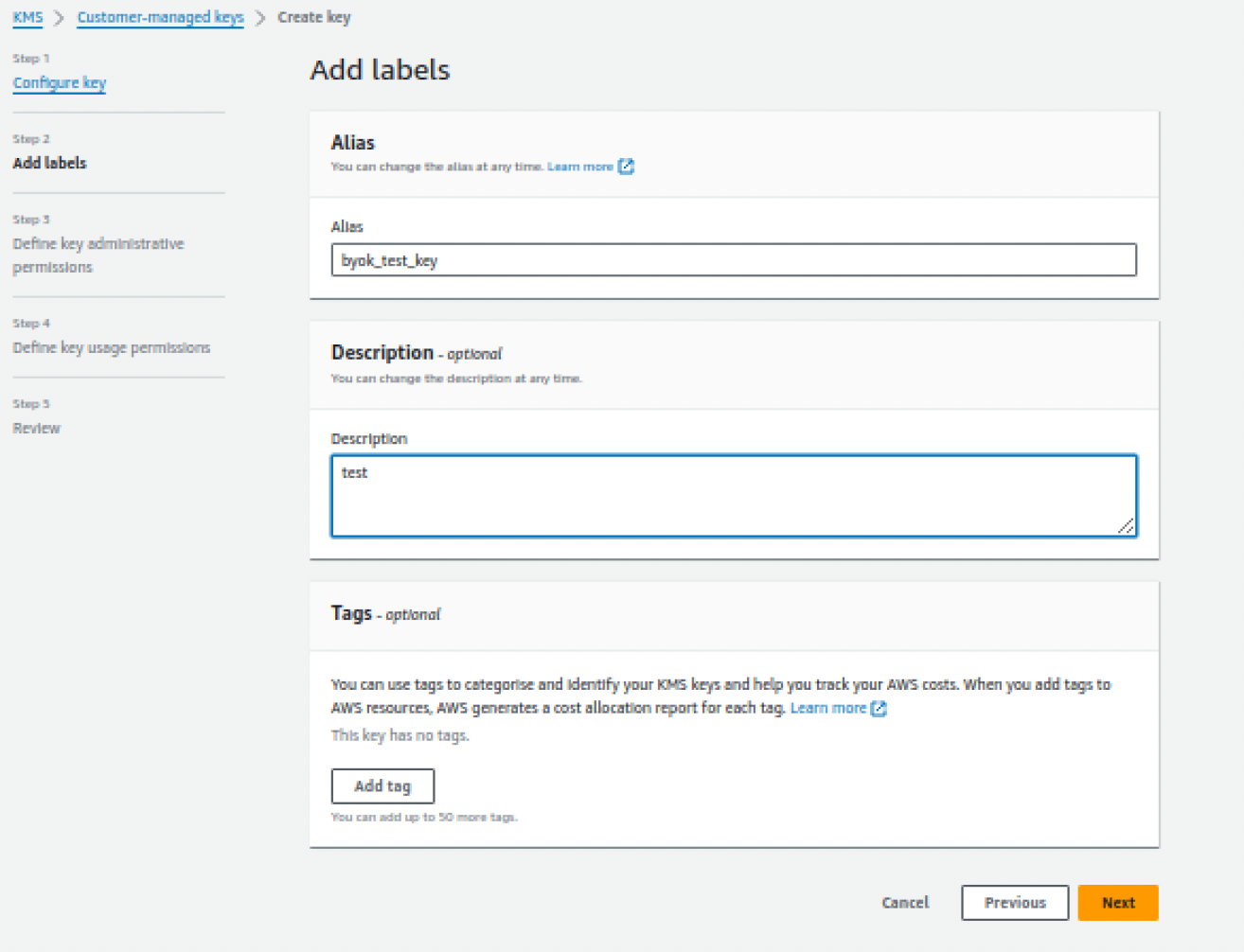
Add Labels
Access permissions are restricted to the root account. No other user or role can delete or modify the key.
2. Download Import Parameters
- Upon key creation, Netcore downloads:
ImportToken.binWrappingPublicKey.binREADME.txt
- Netcore shares the
WrappingPublicKey.binandREADME.txtwith the customer to prepare the wrapped key.
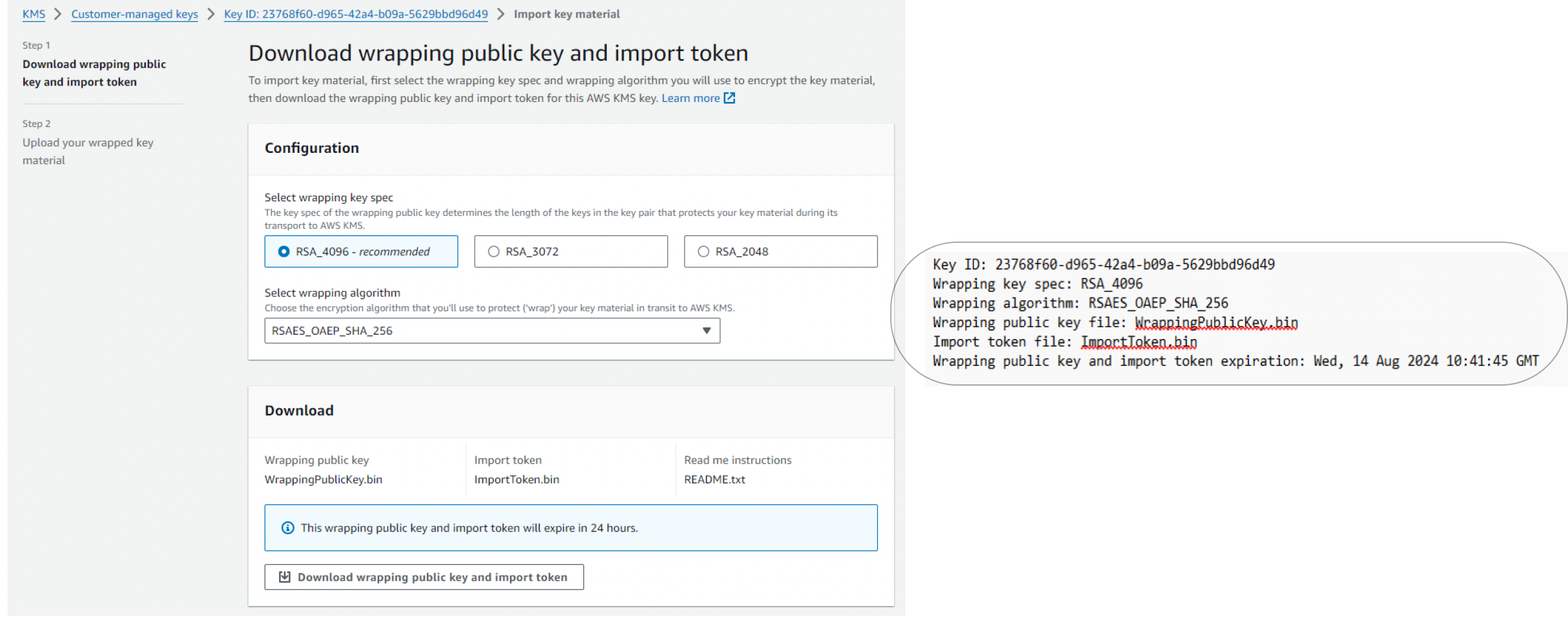
3. Customer Prepares Wrapped Key
The customer:
- Uses the provided wrapping public key.
- Encrypts (wraps) their secret encryption key.
- Generates
CustomerEncryptionKey.bin.
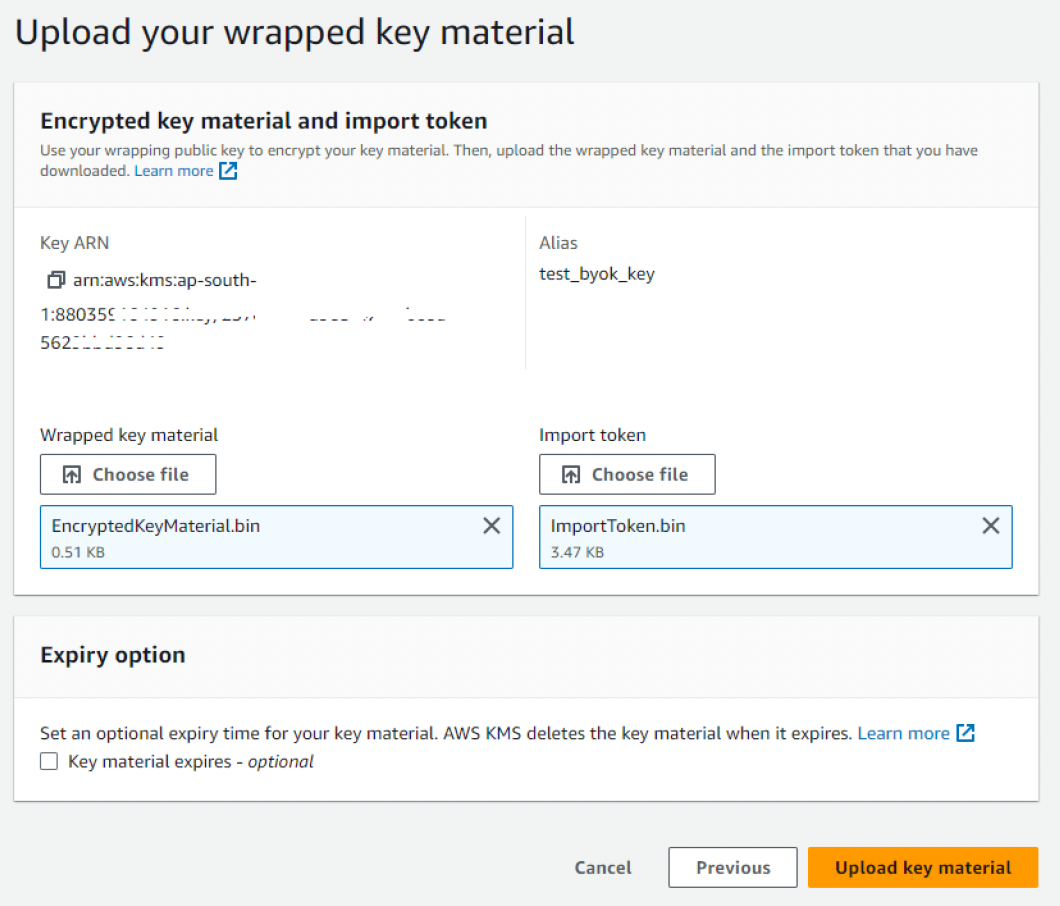
4. Netcore Imports Wrapped Key
Performed within 24 hours of generating the import token.
- Go to the CMK > Import Key Material
- Upload:
CustomerEncryptionKey.binImportToken.bin- Optional: Set key material expiration
Refer to the documentation of AWS here.
- Confirm import
5. Enable Data Encryption
- CMK is linked to Netcore systems.
- Database volumes store data is encrypted using the key.
Ths key is used for encrypting the data at your database
Key Rotation Process
- A new CMK is generated.
- A new wrapping key and import token are downloaded.
- Customer wraps a new encryption key.
- Netcore imports the new key.
- Database systems are reconfigured to use the new key.
Minimal downtime may be expected depending on data volume.
Limitations
- Initial setup is manual and may include a one-time fee.
- Not a toggle-based feature; requires coordination.
- Updates to existing contact data may take up to one hour to reflect.
Updated 3 months ago
